
Core Security Products
Industry-leading products to intelligently safeguard critical data
and assets across your entire organization
Leading-Edge Products to Secure Your Organization
Core Security offers leading-edge identity governance and cyber threat products so your organization can take a comprehensive and predictive approach for security risk management. Using our portfolio of market-leading products, your company can streamline IT and business processes, secure critical data, systems, and assets, and reduce risks associated with user access and infrastructure vulnerability.

Identity Governance Products
Core Security provides intelligent and visible identity governance across all your business environments, enabling you to decrease identity-related risks, boost efficiencies, and ensure ongoing regulatory compliance. Our products for identity governance empower your business to do more with less, meet increasing auditor demands, and make your business more secure, while helping it to grow at the same time. This is accomplished through products that provide the intelligent, visual context needed to manage security risks across the enterprise.
View more about each of our leading-edge Identity Governance products:
Penetration Testing Software
To determine the strength of your organizational security, you need to safely exploit your vulnerabilities by thinking like an attacker—and make sure you are getting the most out of your team by arming them with commercially developed and tested exploits. That’s why we offer Core Impact—an easy-to-use penetration testing tool that enables your security team to exploit security weaknesses, increase productivity, and improve efficiencies.
Discover how you can easily replicate attacks to test your defenses and uncover security gaps. Validate the effectiveness of your remediation measures by retesting exploited systems to ensure your defenses are working properly.

Advanced Threat Detection Products
Get complete visibility into network threat-related activities in your organization. Core Security provides advanced threat detection products and the market-leading security information and event manager (SIEM) offering, giving you actionable intelligence and context needed to manage security risks across your enterprise. Our solutions enable you to reduce the risk of compromise by uncovering vulnerabilities—wherever they reside within your environment—and work together to make sure you focus attention where it matters most. Reduce your threat surface and find out which devices are most susceptible to attacks within your organization.
View more about each of our leading threat detection and security monitoring products:
Benefits of Core Security Products
Decrease Your Threat Surface
With a complete view of your accounts, users, and access, you can ensure you have complete insight and control over your network. By continuously prioritizing and testing for risks, you can significantly eliminate vulnerabilities and quickly reduce the impact of potential threats in your organization.
Reduce IT Costs
With the amount of sensitive data organizations must protect, they are constant targets for attacks. Investing in leading-edge products from Core Security enables your company to spend more time protecting your assets and your network—and less time on administrative tasks. Prioritizing risks and addressing your most pressing threats also ensures you can avoid a costly data breach.
Improve Regulatory Compliance
With full insight, context, and actionable intelligence into your organization, you can gain a comprehensive view of your security posture. Monitor, analyze, and troubleshoot in real time to better manage risk, maintain compliance, and meet ongoing regulatory requirements.
Security Information and Event Management (SIEM) Software
Real-time cybersecurity insight and response platform
Identify and Respond to Security Events in Real Time
Rapid Threat Detection and Response
As threats grow more sophisticated, speed is essential. Risks need to be identified and addressed before damage can occur. HelpSystems’ SIEM software, Event Manager, prioritizes security risks in real time. Automated escalation and streamlined incident response with security event management fast-tracks your response time and resolution.
Separate Critical Events from the Noise
Organizations today collect more security data than ever. Many security events require little to no attention, but serious issues require a rapid response. In that sea of security data, it’s easy for important information to be overlooked. Event Manager reduces alert fatigue by identifying and escalating critical security events, enabling security analysts to respond quickly and effectively. In addition to default settings filtering out insignificant information or benign threats, users can fine tune the data they see, and add inclusion/exclusion rules about what exactly should be processed by Event Manager. Additionally, users can adjust within the dashboard itself, selecting and filtering out alerts that appear that they no longer want to view in the future.
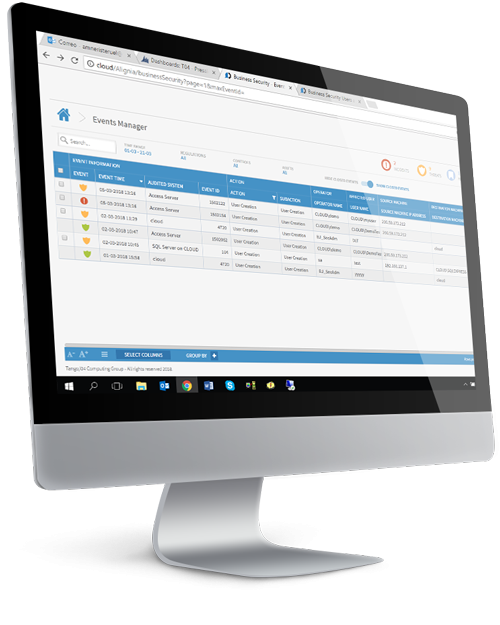
Translate Data into Actionable Intelligence
IT environments are diverse and security events come from a wide variety of sources. These sources display data differently, which requires security analysts to develop fluency and expertise in each format—and increases the opportunity for human error. SIEM software consolidates information in one place and normalizes data, providing context an analyst needs to understand and respond quickly. This enables a faster, more effective response to critical issues.
Since no two organizations are alike, Event Manager allows you to tailor any report as needed with an intuitive interface by selecting, highlighting, and relating any events, threats, and incidents. These fully searchable and shareable reports can also be exported into a variety of formats (PDF, CSV, DOC, XLS).
Complete Audit Trail
Compliance mandates require organizations to prove they know what events are occurring in their environment. Auditors and management teams alike want to see that threat detection and response continues to improve over time. Event Manager records all security events and documents investigations into security events, including notes for closed cases and reported incidents. Reports can also be conveniently scheduled to generate at any time, making it easy to meet compliance requirements and report on security progress over time.
Key Features of Event Manager
Security Event Prioritization
It is impossible to stay ahead of the curve if your security team is buried investigating meaningless security events. Our security information and event management software helps you determine which events are most critical and which events are lower priority. We make the prioritization process easy with out-of-the-box controls that can be adjusted as you see fit.
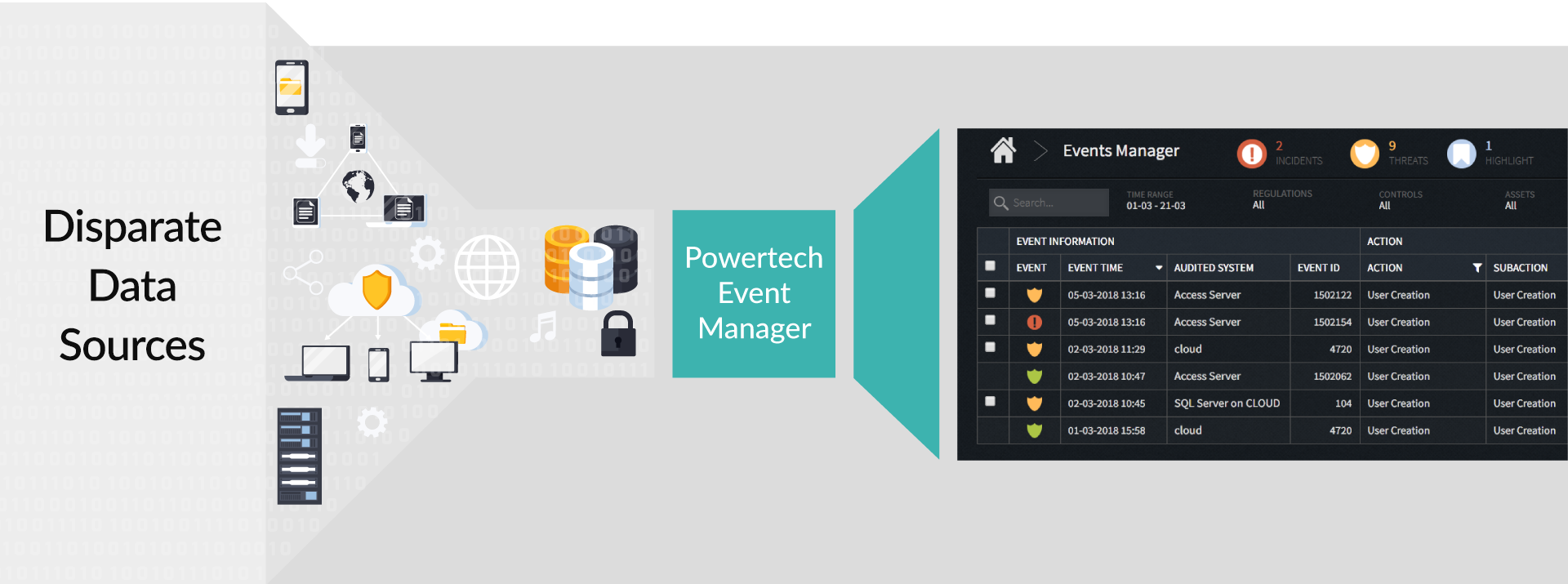
Normalization of Disparate Data Sources
Organizations rely on multiple technologies to run their business. This makes it difficult for security teams to understand the data coming in from these disparate sources. Event Manager turns this data into actionable intelligence by normalizing it into a common format and giving it meaning. Analysts won’t need to understand the nuances of different operating systems, applications, databases, firewalls, or network appliances to know what the data means and what to do with it.

Data Enrichment
Our SIEM software provides additional context behind security events for quick and thorough response. Data enrichment with Event Manager puts all of the necessary event details and forensic analysis at your fingertips.

Real-time Threat Detection
In order to minimize the impact of a breach, you have to detect threats quickly. Event Manager logs, correlates, and prioritizes events in real time—giving your team a head start to resolve and mitigate threats before they result in a devastating breach.
Streamlined Incident Response
Our security and information event management software allows you to automate escalation of events to the right person and manage any cases that require further investigation. Managing the investigation of an event or incident is easy with Event Manager – making your team more efficient.

Out-of-the-Box Security
As you connect new data sources, like Oracle databases, SWIFT, or AWS Cloudtrail, Event Manager automatically applies the appropriate logic to normalize the data and assign the appropriate escalation. Our out-of-the-box security connections make it easy to get started quickly and are easily configurable.

Security and Compliance Reporting
IT operations and security teams alike are required to provide reports to both auditors and executives on a regular basis. Most organizations also need to comply with multiple regulations, which adds to the complexity and reporting effort. Compile these reports easily with Event Manager. It logs all event and incident response activity for easy reporting. It can even help you show how your security posture is improving over time.
Strong Alignment with Other Solutions
Out-of-the-box integrations with Powertech Security Auditor, Powertech Identity & Access Manager, Intermapper, and many more third-party applications enhances efficiency by allowing for a seamless transition between products. Assess security policies, oversee privileged access, and monitor your network all in one streamlined, centralized profile.
SIEM Integration for Meaningful Insight
Our SIEM platform enriches the data to provide your team with helpful insight. Event Manager provides normalized event data for an extensive number of platforms and provides simple support for integrating audit data through a variety of standard technologies like Windows Eventlog, Syslog, Database and log files. Event Manager leaves no device behind, providing a tool for converting custom data sources so they are also fully integrated.
One-Size-Fits-All SIEM Solution
Organizations have different requirements and varying degrees of resources. Event Manager is a security information and event management platform that can take threat detection and response to the next level while remaining easy-to-use, making it a sophisticated and flexible solution suitable for organizations of all sizes and industries to rely on.
For instance, small businesses or those with limited resources can utilize our free SIEM to help them proactively manage risk with their existing staff. And large enterprises dealing with an unmanageable number of security events can rely on Event Manager to make rapid threat detection and response attainable for substantial, complex networks and high volumes of security events to manage.
See What Powertech Event Manager Can Do
Powertech Event Manager relays actionable intelligence that enables you to manage potential vulnerabilities proactively, protecting your business and your customers from devastating data breaches. Watch this short demo to see its features in action, including:
- Personalized dashboards
- Streamlined incident response
- Data enrichment
- Built in and tailored integrations
- Complete audit trails and scheduled reporting


